本文最后更新于:2021-08-13 下午
初探
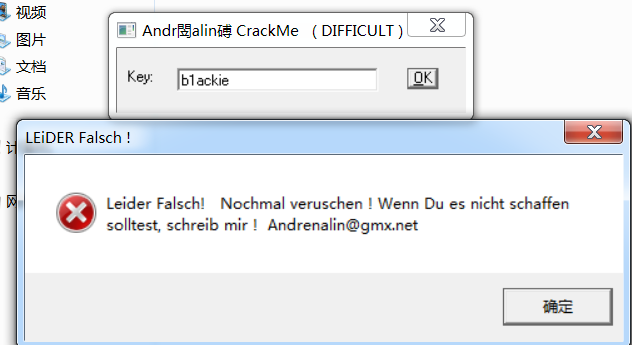
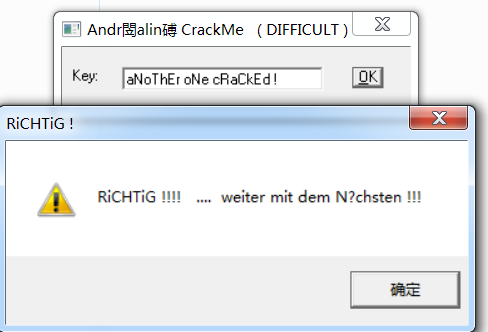
打开程序,看到只有一个输入key的地方,尝试输入发现弹出错误的弹窗。
分析
无壳,用VB语言编写的。
使用OD打开,直接搜索错误的字符串,可以定位到关键的跳转,在上面就是一个比较函数,而其中又有一串字符串”kXy^rO|yXom\kMuOn*+”,这个应该就是用来比较的了吧,函数头部下断开始分析。
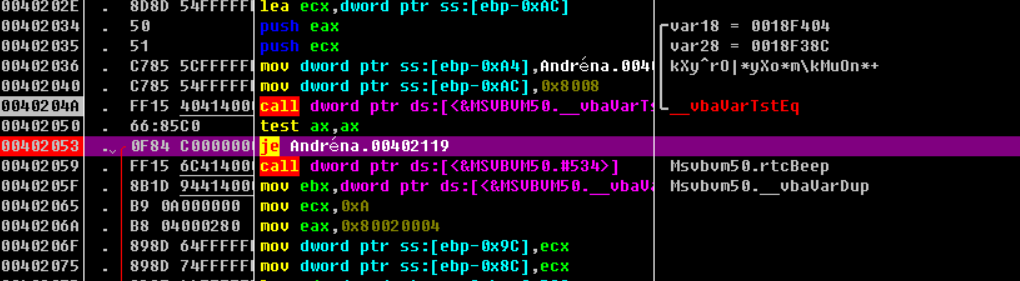
流程较短也比较简单,前面还有一个获取输入的长度,就不在分析了,直接看关键的计算部分。
获取输入的每一位KEY加上0xA形成新的KEY最后再与”kXy^rO|yXom\kMuOn*+”作比较。那么用这段字符减去A就可以得到输入的key了,下面开始写注册机
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
51
52
53
54
55
56
57
58
59
60
61
62
63
64
65
| 00401F68 > /85C0 test eax,eax
00401F6A . |0F84 BB000000 je Andréna.0040202B
00401F70 . |8D55 94 lea edx,dword ptr ss:[ebp-0x6C]
00401F73 . |8D45 DC lea eax,dword ptr ss:[ebp-0x24]
00401F76 . |52 push edx
00401F77 . |50 push eax
00401F78 . |C745 9C 01000>mov dword ptr ss:[ebp-0x64],0x1
00401F7F . |C745 94 02000>mov dword ptr ss:[ebp-0x6C],0x2
00401F86 . |FF15 90414000 call dword ptr ds:[<&MSVBVM50.__vbaI4Var>
00401F8C . |8D4D BC lea ecx,dword ptr ss:[ebp-0x44]
00401F8F . |50 push eax
00401F90 . |8D55 84 lea edx,dword ptr ss:[ebp-0x7C]
00401F93 . |51 push ecx
00401F94 . |52 push edx
00401F95 . |FF15 34414000 call dword ptr ds:[<&MSVBVM50.#632>]
00401F9B . |8D45 84 lea eax,dword ptr ss:[ebp-0x7C]
00401F9E . |8D4D A8 lea ecx,dword ptr ss:[ebp-0x58]
00401FA1 . |50 push eax
00401FA2 . |51 push ecx
00401FA3 . |FF15 64414000 call dword ptr ds:[<&MSVBVM50.__vbaStrVa>
00401FA9 . |50 push eax
00401FAA . |FF15 08414000 call dword ptr ds:[<&MSVBVM50.#516>]
00401FB0 . |66:05 0A00 add ax,0xA
00401FB4 . |0F80 B0020000 jo Andréna.0040226A
00401FBA . |0FBFD0 movsx edx,ax
00401FBD . |52 push edx
00401FBE . |FF15 70414000 call dword ptr ds:[<&MSVBVM50.#537>]
00401FC4 . |8985 7CFFFFFF mov dword ptr ss:[ebp-0x84],eax
00401FCA . |8D45 CC lea eax,dword ptr ss:[ebp-0x34]
00401FCD . |8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C]
00401FD3 . |50 push eax
00401FD4 . |8D95 64FFFFFF lea edx,dword ptr ss:[ebp-0x9C]
00401FDA . |51 push ecx
00401FDB . |52 push edx
00401FDC . |C785 74FFFFFF>mov dword ptr ss:[ebp-0x8C],0x8
00401FE6 . |FFD3 call ebx
00401FE8 . |8BD0 mov edx,eax
00401FEA . |8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
00401FED . |FFD6 call esi
00401FEF . |8D4D A8 lea ecx,dword ptr ss:[ebp-0x58]
00401FF2 . |FF15 B0414000 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>
00401FF8 . |8D85 74FFFFFF lea eax,dword ptr ss:[ebp-0x8C]
00401FFE . |8D4D 84 lea ecx,dword ptr ss:[ebp-0x7C]
00402001 . |50 push eax
00402002 . |8D55 94 lea edx,dword ptr ss:[ebp-0x6C]
00402005 . |51 push ecx
00402006 . |52 push edx
00402007 . |6A 03 push 0x3
00402009 . |FFD7 call edi
0040200B . |83C4 10 add esp,0x10
0040200E . |8D85 ECFEFFFF lea eax,dword ptr ss:[ebp-0x114]
00402014 . |8D8D FCFEFFFF lea ecx,dword ptr ss:[ebp-0x104]
0040201A . |8D55 DC lea edx,dword ptr ss:[ebp-0x24]
0040201D . |50 push eax
0040201E . |51 push ecx
0040201F . |52 push edx
00402020 . |FF15 A4414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>
00402026 .^\E9 3DFFFFFF jmp Andréna.00401F68
0040202B > \8D45 CC lea eax,dword ptr ss:[ebp-0x34]
0040202E . 8D8D 54FFFFFF lea ecx,dword ptr ss:[ebp-0xAC]
00402034 . 50 push eax
00402035 . 51 push ecx
00402036 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>
00402040 . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8008
0040204A . FF15 40414000 call dword ptr ds:[<&MSVBVM50.__vbaVarTs>
|
注册机编写
| #include <Windows.h>
#include <stdio.h>
int main()
{
char key[] = "kXy^rO|*yXo*m\\kMuOn*+";
for (int i = 0; i < strlen(key); i++)
{
key[i] = key[i] - 0xA;
}
printf("%s", key);
return 0;
}
|
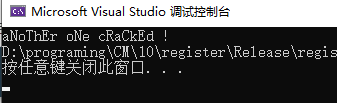
输入正确的KEY
总结
流程还是比较简单的,算法也很简单,总体上来讲难度不大。




