本文最后更新于:2021-08-09 晚上
前言
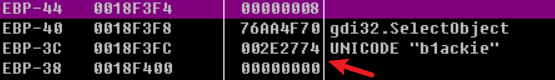
这个VB的程序,调用的时候都是传入一个地址,然后地址直接查看是什么也看不到,没有什么有用的,分析起来看得人一头雾水。查了资料之后才知道,VB的变量特征是前两个4字节都是一些数据类型,第三个四字节才是变量,相当于是首地址+0x8的地方。
比如此时寄存器中值是18F3F4,它实际存储的值是18F3FC处的数据。
初探
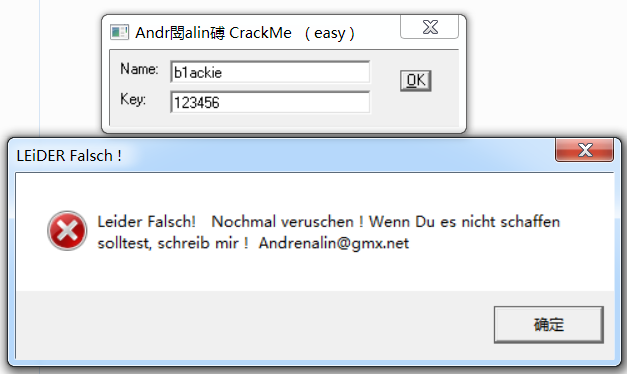
打开程序,看到需要输入name和key输入后弹出错误的提示框。
分析
查壳,无壳是用VB语言写的。
使用OD搜索错误提示的字符串可以搜索到直接定位到关键跳转。在函数头部下断开始分析。
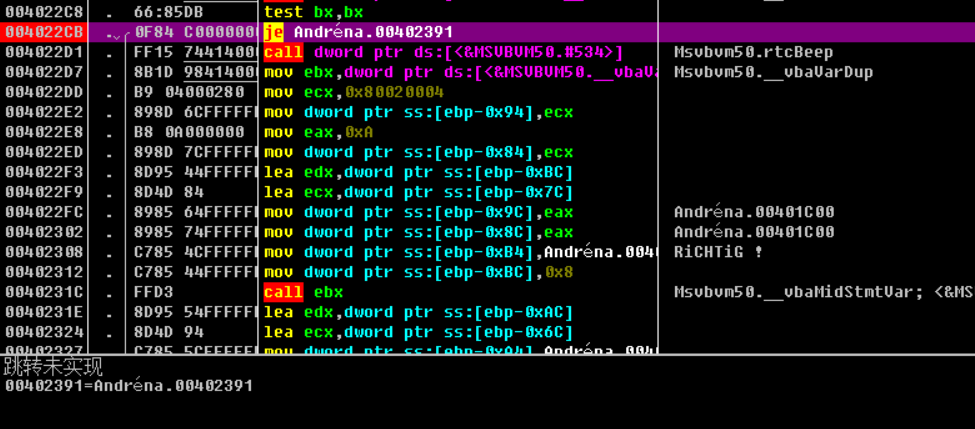
先获取了输入的name的长度,但是这个长度后面好像是没有参加任何运算的,我没有分析到有参加运算的地方。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
| 004020EF . 51 push ecx ; /Step8 = 0018F3E0
004020F0 . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C] ; |
004020F3 . BB 02000000 mov ebx,0x2 ; |
004020F8 . 52 push edx ; |/var18 = 0018F3BC
004020F9 . 50 push eax ; ||retBuffer8 = 0018F3CC
004020FA . 899D 54FFFFFF mov dword ptr ss:[ebp-0xAC],ebx ; ||
00402100 . 899D 44FFFFFF mov dword ptr ss:[ebp-0xBC],ebx ; ||
00402106 . FF15 18414000 call dword ptr ds:[<&MSVBVM50.__vbaLenVa>; |\__vbaLenVar
0040210C . 8D8D 44FFFFFF lea ecx,dword ptr ss:[ebp-0xBC] ; |
00402112 . 50 push eax ; |End8 = 0018F3CC
00402113 . 8D95 E8FEFFFF lea edx,dword ptr ss:[ebp-0x118] ; |
00402119 . 51 push ecx ; |Start8 = 0018F3E0
0040211A . 8D85 F8FEFFFF lea eax,dword ptr ss:[ebp-0x108] ; |
00402120 . 52 push edx ; |TMPend8 = 0018F3BC
00402121 . 8D4D DC lea ecx,dword ptr ss:[ebp-0x24] ; |
00402124 . 50 push eax ; |TMPstep8 = 0018F3CC
00402125 . 51 push ecx ; |Counter8 = 0018F3E0
00402126 . FF15 20414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>; \__vbaVarForInit
|
首先是对于name 的操作,获取了每一位的ascii码值,然后相加。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
36
37
38
39
40
41
42
43
44
45
46
47
48
49
50
| 00402134 . /0F84 9C000000 je Andréna.004021D6
0040213A . |8D55 94 lea edx,dword ptr ss:[ebp-0x6C]
0040213D . |8D45 DC lea eax,dword ptr ss:[ebp-0x24]
00402140 . |52 push edx
00402141 . |50 push eax
00402142 . |C745 9C 01000>mov dword ptr ss:[ebp-0x64],0x1
00402149 . |895D 94 mov dword ptr ss:[ebp-0x6C],ebx
0040214C . |FF15 90414000 call dword ptr ds:[<&MSVBVM50.__vbaI4Var>; Msvbvm50.__vbaI4Var
00402152 . |8D4D BC lea ecx,dword ptr ss:[ebp-0x44] ; |
00402155 . |50 push eax ; |Start = 0x18F3CC
00402156 . |8D55 84 lea edx,dword ptr ss:[ebp-0x7C] ; |
00402159 . |51 push ecx ; |dString8 = 0018F3E0
0040215A . |52 push edx ; |RetBUFFER = 0018F3BC
0040215B . |FF15 38414000 call dword ptr ds:[<&MSVBVM50.#632>] ; \获取每一位
00402161 . |8D45 84 lea eax,dword ptr ss:[ebp-0x7C]
00402164 . |8D4D A8 lea ecx,dword ptr ss:[ebp-0x58]
00402167 . |50 push eax ; /String8 = 0018F3CC
00402168 . |51 push ecx ; |ARG2 = 0018F3E0
00402169 . |FF15 70414000 call dword ptr ds:[<&MSVBVM50.__vbaStrVa>; \__vbaStrVarVal
0040216F . |50 push eax ; /String = "�"
00402170 . |FF15 0C414000 call dword ptr ds:[<&MSVBVM50.#516>] ; \转为ascii
00402176 . |66:8985 4CFFF>mov word ptr ss:[ebp-0xB4],ax
0040217D . |8D55 CC lea edx,dword ptr ss:[ebp-0x34]
00402180 . |8D85 44FFFFFF lea eax,dword ptr ss:[ebp-0xBC]
00402186 . |52 push edx ; /var18 = 0018F3BC
00402187 . |8D8D 74FFFFFF lea ecx,dword ptr ss:[ebp-0x8C] ; |
0040218D . |50 push eax ; |var28 = 0018F3CC
0040218E . |51 push ecx ; |saveto8 = 0018F3E0
0040218F . |899D 44FFFFFF mov dword ptr ss:[ebp-0xBC],ebx ; |
00402195 . |FF15 94414000 call dword ptr ds:[<&MSVBVM50.__vbaVarAd>; \相加
0040219B . |8BD0 mov edx,eax
0040219D . |8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
004021A0 . |FFD6 call esi ; Msvbvm50.__vbaVarMove
004021A2 . |8D4D A8 lea ecx,dword ptr ss:[ebp-0x58]
004021A5 . |FF15 B8414000 call dword ptr ds:[<&MSVBVM50.__vbaFreeS>; Msvbvm50.__vbaFreeStr
004021AB . |8D55 84 lea edx,dword ptr ss:[ebp-0x7C]
004021AE . |8D45 94 lea eax,dword ptr ss:[ebp-0x6C]
004021B1 . |52 push edx
004021B2 . |50 push eax
004021B3 . |53 push ebx
004021B4 . |FFD7 call edi ; Msvbvm50.__vbaFreeVarList
004021B6 . |83C4 0C add esp,0xC
004021B9 . |8D8D E8FEFFFF lea ecx,dword ptr ss:[ebp-0x118]
004021BF . |8D95 F8FEFFFF lea edx,dword ptr ss:[ebp-0x108]
004021C5 . |8D45 DC lea eax,dword ptr ss:[ebp-0x24]
004021C8 . |51 push ecx ; /TMPend8 = 0018F3E0
004021C9 . |52 push edx ; |TMPstep8 = 0018F3BC
004021CA . |50 push eax ; |Counter8 = 0018F3CC
004021CB . |FF15 AC414000 call dword ptr ds:[<&MSVBVM50.__vbaVarFo>; \__vbaVarForNext
004021D1 .^|E9 5CFFFFFF jmp Andréna.00402132
|
然后所有name相加的结果乘以0x499602D2
| 004021D6 > \8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
004021D9 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC]
004021DF . 51 push ecx
004021E0 . 8D45 94 lea eax,dword ptr ss:[ebp-0x6C]
004021E3 . 52 push edx
004021E4 . 50 push eax
004021E5 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],0x499602D2
004021EF . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x3
004021F9 . FF15 5C414000 call dword ptr ds:[<&MSVBVM50.__vbaVarMu>
|
这个值再转为十进制的字符串。
可以看到这个值和计算器计算出来的是一样的。
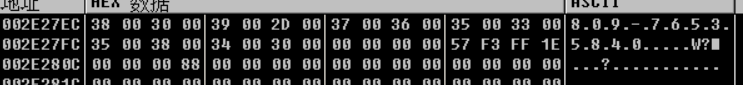
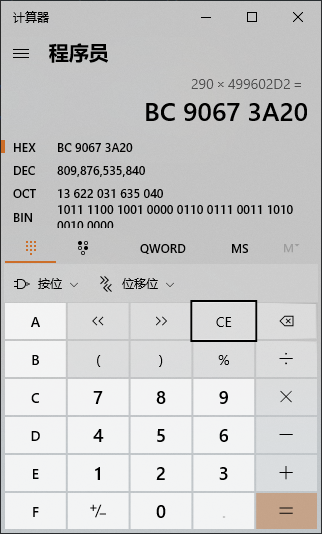
最后就是使用“-”替换到第四位和第九位的字符。
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
| 00402206 . 8B1D A0414000 mov ebx,dword ptr ds:[<&MSVBVM50.__vbaMi>; Msvbvm50.__vbaMidStmtVar
0040220C . 8D4D CC lea ecx,dword ptr ss:[ebp-0x34]
0040220F . 51 push ecx
00402210 . 6A 04 push 0x4
00402212 . 8D95 54FFFFFF lea edx,dword ptr ss:[ebp-0xAC]
00402218 . 6A 01 push 0x1
0040221A . 52 push edx
0040221B . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>; -
00402225 . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8
0040222F . FFD3 call ebx ; <&MSVBVM50.__vbaMidStmtVar>
00402231 . 8D45 CC lea eax,dword ptr ss:[ebp-0x34]
00402234 . 8D8D 54FFFFFF lea ecx,dword ptr ss:[ebp-0xAC]
0040223A . 50 push eax
0040223B . 6A 09 push 0x9
0040223D . 6A 01 push 0x1
0040223F . 51 push ecx
00402240 . C785 5CFFFFFF>mov dword ptr ss:[ebp-0xA4],Andréna.0040>; -
0040224A . C785 54FFFFFF>mov dword ptr ss:[ebp-0xAC],0x8
00402254 . FFD3 call ebx
|
下面开始编写注册机
注册机编写
根据以上分析的结果
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
| #include <stdio.h>
#include <Windows.h>
int main()
{
printf("输入name\n");
char name[20];
gets_s(name);
long long key = 0;
int len = strlen(name);
for (int i = 0; i < len; i++)
{
key += name[i];
}
key *= 0x499602D2;
char buf[30];
sprintf(buf, "%lld", key);
buf[3] = '-';
buf[8] = '-';
printf("你的key是:\n%s", buf);
return 0;
}
|
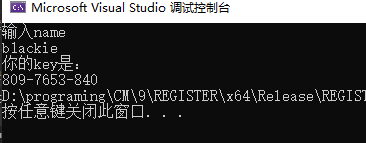
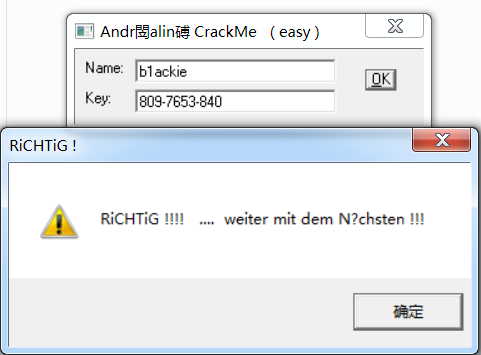
总结
分析起来不难,主要是VB的特性让人很折磨。







