本文最后更新于:2021-08-09 晚上
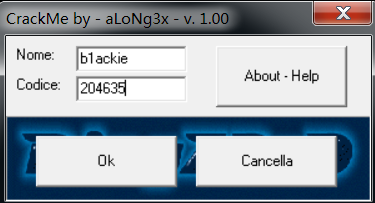
初探 打开程序如下看到OK是不可点击的,是一个灰色按钮。
点击about查看一下,可以看到我们需要让两个按钮都消失以便可以看到Ringzer0的logo
那么先想办法让OK变得可以点击吧。
分析 查看壳,发现未加壳,是用Delphi写的
使用API断点,给IsEnableWindow下断,但是发现怎么都无法断下来,说明肯定是有条件的,而当前还没有满足这个条件。
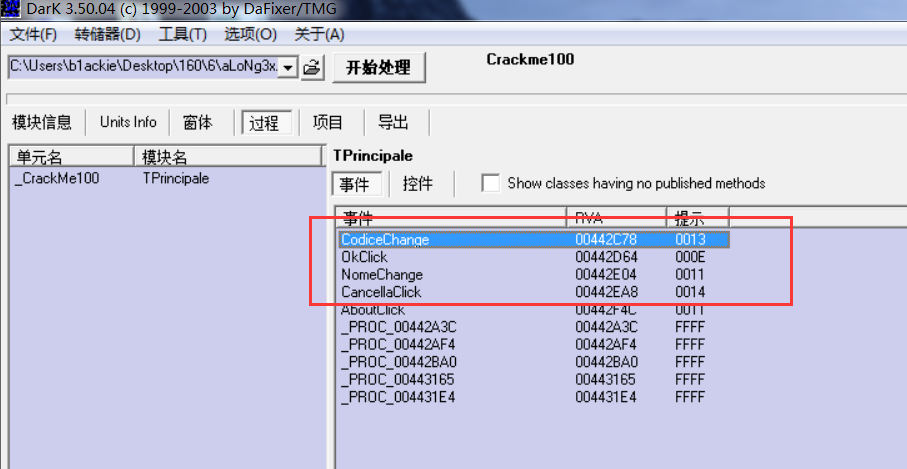
使用dedark工具帮忙查看,直接分析真的是太难找了,可以看到主要四个事件,这四个事件应该比较关键
根据函数地址找到函数下好断点之后,查看可以发现nomechange和codicechange几乎是一样的,将两处明显的跳转更改条件使跳转失效,让程序跑起来后都会断在之前下的API断点上。那么它们都是比较关键的地方。
第一个关键跳转都是判断eax+0x47这个地址的值是否等于0,而第二个跳转都是先调用了00442A3C这个函数。
nomechange:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 00442E04 /. 55 push ebp ; nomeChange00442E05 |. 8 BEC mov ebp,esp00442E07 |. 6 A 00 push 0 x0 00442E09 |. 6 A 00 push 0 x0 00442E0B |. 53 push ebx00442E0C |. 8 BD8 mov ebx,eax00442E0E |. 33 C0 xor eax,eax00442E10 |. 55 push ebp00442E11 |. 68 9 B2 E4400 push aLoNg3 x_.00442 E9 B00442E16 |. 64 :FF30 push dword ptr fs:[eax]00442E19 |. 64 :8920 mov dword ptr fs:[eax],esp00442E1C |. 8 B83 D0020000 mov eax,dword ptr ds:[ebx+0 x2 D0 ]00442E22 |. 8078 47 00 cmp byte ptr ds:[eax+0 x47 ],0 x0 00442E26 |. 75 0 F jnz short aLoNg3 x_.00442 E37 ; 关键跳转1 00442E28 |. B2 01 mov dl,0 x1 00442E2A |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC]00442E30 |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442E32 |. FF51 60 call dword ptr ds:[ecx+0 x60 ] ; IsEnableWindow00442E35 |. EB 49 jmp short aLoNg3 x_.00442 E80 00442E37 |> 8 D55 FC lea edx,dword ptr ss:[ebp-0 x4 ]00442E3A |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442E40 |. E8 7 B04 FEFF call aLoNg3 x_.004232 C0 00442E45 |. 8 B45 FC mov eax,dword ptr ss:[ebp-0 x4 ] ; user32 .75 B17276 00442E48 |. 50 push eax00442E49 |. 8 D55 F8 lea edx,dword ptr ss:[ebp-0 x8 ]00442E4C |. 8 B83 DC020000 mov eax,dword ptr ds:[ebx+0 x2 DC] ; comctl_1 .74646957 00442E52 |. E8 6904 FEFF call aLoNg3 x_.004232 C0 00442E57 |. 8 B45 F8 mov eax,dword ptr ss:[ebp-0 x8 ]00442E5A |. 5 A pop edx ; aLoNg3 x_.0041 E13 E00442E5B |. E8 DCFBFFFF call aLoNg3 x_.00442 A3 C00442E60 |. 84 C0 test al,al00442E62 |. 74 0 F je short aLoNg3 x_.00442 E73 ; 关键跳转2 00442E64 |. B2 01 mov dl,0 x1 00442E66 |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC]00442E6C |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442E6E |. FF51 60 call dword ptr ds:[ecx+0 x60 ] ; IsEnableWindow00442E71 |. EB 0 D jmp short aLoNg3 x_.00442 E80 00442E73 |> 33 D2 xor edx,edx00442E75 |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC]00442E7B |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442E7D |. FF51 60 call dword ptr ds:[ecx+0 x60 ]00442E80 |> 33 C0 xor eax,eax00442E82 |. 5 A pop edx ; aLoNg3 x_.0041 E13 E00442E83 |. 59 pop ecx ; aLoNg3 x_.0041 E13 E00442E84 |. 59 pop ecx ; aLoNg3 x_.0041 E13 E00442E85 |. 64 :8910 mov dword ptr fs:[eax],edx00442E88 |. 68 A22 E4400 push aLoNg3 x_.00442 EA2 00442E8D |> 8 D45 F8 lea eax,dword ptr ss:[ebp-0 x8 ]00442E90 |. BA 02000000 mov edx,0 x2 00442E95 |. E8 4209 FCFF call aLoNg3 x_.004037 DC00442E9A \. C3 retn00442E9B .^ E9 D803 FCFF jmp aLoNg3 x_.00403278 00442EA0 .^ EB EB jmp short aLoNg3 x_.00442 E8 D00442EA2 . 5 B pop ebx ; aLoNg3 x_.0041 E13 E00442EA3 . 59 pop ecx ; aLoNg3 x_.0041 E13 E00442EA4 . 59 pop ecx ; aLoNg3 x_.0041 E13 E00442EA5 . 5 D pop ebp ; aLoNg3 x_.0041 E13 E00442EA6 . C3 retn
codicechange:
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 00442C78 /. 55 push ebp ; codiceChange00442C79 |. 8 BEC mov ebp,esp00442C7B |. 33 C9 xor ecx,ecx00442C7D |. 51 push ecx00442C7E |. 51 push ecx00442C7F |. 51 push ecx00442C80 |. 51 push ecx00442C81 |. 53 push ebx00442C82 |. 56 push esi00442C83 |. 8 BD8 mov ebx,eax00442C85 |. 33 C0 xor eax,eax00442C87 |. 55 push ebp00442C88 |. 68 562 D4400 push aLoNg3 x_.00442 D56 00442C8D |. 64 :FF30 push dword ptr fs:[eax]00442C90 |. 64 :8920 mov dword ptr fs:[eax],esp00442C93 |. 8 D55 F8 lea edx,dword ptr ss:[ebp-0 x8 ]00442C96 |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442C9C |. E8 1 F06 FEFF call aLoNg3 x_.004232 C0 00442CA1 |. 8 B45 F8 mov eax,dword ptr ss:[ebp-0 x8 ]00442CA4 |. 8 D55 FC lea edx,dword ptr ss:[ebp-0 x4 ]00442CA7 |. E8 ACFCFBFF call aLoNg3 x_.00402958 00442CAC |. 8 BF0 mov esi,eax00442CAE |. 837 D FC 00 cmp dword ptr ss:[ebp-0 x4 ],0 x0 00442CB2 |. 74 18 je short aLoNg3 x_.00442 CCC00442CB4 |. 8 D55 F4 lea edx,dword ptr ss:[ebp-0 xC]00442CB7 |. 8 BC6 mov eax,esi00442CB9 |. E8 8249 FCFF call aLoNg3 x_.00407640 00442CBE |. 8 B55 F4 mov edx,dword ptr ss:[ebp-0 xC]00442CC1 |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442CC7 |. E8 2406 FEFF call aLoNg3 x_.004232 F0 00442CCC |> 8 B83 D0020000 mov eax,dword ptr ds:[ebx+0 x2 D0 ]00442CD2 |. 8078 47 00 cmp byte ptr ds:[eax+0 x47 ],0 x0 00442CD6 |. 75 0 F jnz short aLoNg3 x_.00442 CE7 ; 关键跳转1 00442CD8 |. B2 01 mov dl,0 x1 00442CDA |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC] ; comctl_1 .74646957 00442CE0 |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442CE2 |. FF51 60 call dword ptr ds:[ecx+0 x60 ] ; IsEnableWindow00442CE5 |. EB 49 jmp short aLoNg3 x_.00442 D30 00442CE7 |> 8 D55 F8 lea edx,dword ptr ss:[ebp-0 x8 ]00442CEA |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442CF0 |. E8 CB05 FEFF call aLoNg3 x_.004232 C0 00442CF5 |. 8 B45 F8 mov eax,dword ptr ss:[ebp-0 x8 ]00442CF8 |. 50 push eax00442CF9 |. 8 D55 F0 lea edx,dword ptr ss:[ebp-0 x10 ]00442CFC |. 8 B83 DC020000 mov eax,dword ptr ds:[ebx+0 x2 DC]00442D02 |. E8 B905 FEFF call aLoNg3 x_.004232 C0 00442D07 |. 8 B45 F0 mov eax,dword ptr ss:[ebp-0 x10 ]00442D0A |. 5 A pop edx ; aLoNg3 x_.0041 E13 E00442D0B |. E8 2 CFDFFFF call aLoNg3 x_.00442 A3 C00442D10 |. 84 C0 test al,al00442D12 |. 74 0 F je short aLoNg3 x_.00442 D23 ; 关键跳转2 00442D14 |. B2 01 mov dl,0 x1 00442D16 |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC] ; comctl_1 .74646957 00442D1C |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442D1E |. FF51 60 call dword ptr ds:[ecx+0 x60 ] ; IsEnableWindow00442D21 |. EB 0 D jmp short aLoNg3 x_.00442 D30 00442D23 |> 33 D2 xor edx,edx00442D25 |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC] ; comctl_1 .74646957 00442D2B |. 8 B08 mov ecx,dword ptr ds:[eax] ; aLoNg3 x_.0044282 C00442D2D |. FF51 60 call dword ptr ds:[ecx+0 x60 ]00442D30 |> 33 C0 xor eax,eax00442D32 |. 5 A pop edx ; aLoNg3 x_.0041 E13 E00442D33 |. 59 pop ecx ; aLoNg3 x_.0041 E13 E00442D34 |. 59 pop ecx ; aLoNg3 x_.0041 E13 E00442D35 |. 64 :8910 mov dword ptr fs:[eax],edx00442D38 |. 68 5 D2 D4400 push aLoNg3 x_.00442 D5 D00442D3D |> 8 D45 F0 lea eax,dword ptr ss:[ebp-0 x10 ]00442D40 |. E8 730 AFCFF call aLoNg3 x_.004037 B8 00442D45 |. 8 D45 F4 lea eax,dword ptr ss:[ebp-0 xC]00442D48 |. E8 6 B0 AFCFF call aLoNg3 x_.004037 B8 00442D4D |. 8 D45 F8 lea eax,dword ptr ss:[ebp-0 x8 ]00442D50 |. E8 630 AFCFF call aLoNg3 x_.004037 B8 00442D55 \. C3 retn
尝试在eax+0x47这下硬件写入断点,发现并不能断下来,说明还是没有满足某个条件。
看第二个关键函数,可以看到一个计算,通过用户名算出serial,懒得再解释了QAQ,直接看下面代码吧。
00442A8E |. B8 01000000 mov eax,0 x1 00442A93 |> 8 B4 D FC /mov ecx,dword ptr ss:[ebp-0 x4 ] ; user32 .75 B17276 00442A96 |. 0 FB64 C01 FF |movzx ecx,byte ptr ds:[ecx+eax-0 x1 ]00442A9B |. 8 B75 FC |mov esi,dword ptr ss:[ebp-0 x4 ] ; user32 .75 B17276 00442A9E |. 0 FB63406 |movzx esi,byte ptr ds:[esi+eax]00442AA2 |. 0 FAFCE |imul ecx,esi00442AA5 |. 0 FAFC8 |imul ecx,eax00442AA8 |. 03 D9 |add ebx,ecx00442AAA |. 40 |inc eax00442AAB |. 4 A |dec edx00442AAC |.^ 75 E5 \jnz short aLoNg3 x_.00442 A93 00442AAE |> 8 B45 F8 mov eax,dword ptr ss:[ebp-0 x8 ]00442AB1 |. E8 BA4 BFCFF call aLoNg3 x_.00407670 00442AB6 |. 2 BD8 sub ebx,eax00442AB8 |. 81 FB 9 A020000 cmp ebx,0 x29 A00442ABE |. 75 04 jnz short aLoNg3 x_.00442 AC4
int len = strlen (szname);int sum = len;int temp = 1 ;for (int i = 0 ; i < len - 1 ; i++) {1 ]) * temp) + sum;int serial;0x29A ;printf ("%d\n" , serial);
输入发现OK按钮已经亮了
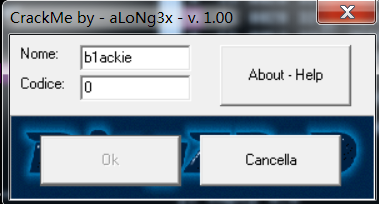
点击OK按钮发现,没有用,codice清0,然后OK又灰色了。
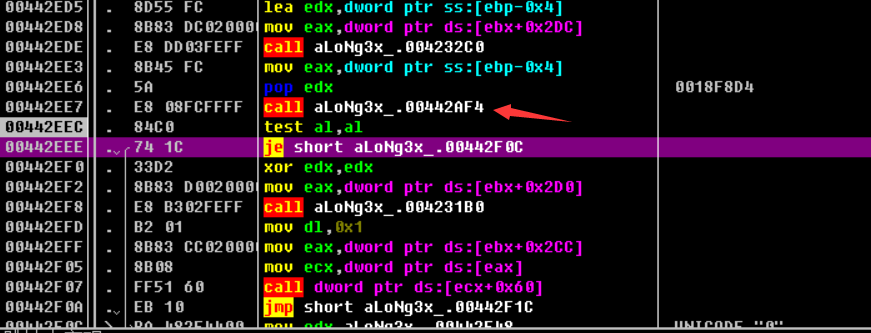
从OK按钮入手,发现刚进来的第一个跳转就是熟悉的判断条件,说明程序并不是直接点击OK的,在这之前肯定还有一个条件要满足的。先继续在这里看一下,修改这个条件往下走,可以看到第二个跳转,修改这个跳转,按钮就会小时,经过分析之前这个函数就是算法。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 00442D64 /. 55 push ebp00442D65 |. 8 BEC mov ebp,esp00442D67 |. 6 A 00 push 0 x0 00442D69 |. 53 push ebx00442D6A |. 8 BD8 mov ebx,eax00442D6C |. 33 C0 xor eax,eax00442D6E |. 55 push ebp00442D6F |. 68 ED2 D4400 push aLoNg3 x_.00442 DED00442D74 |. 64 :FF30 push dword ptr fs:[eax]00442D77 |. 64 :8920 mov dword ptr fs:[eax],esp00442D7A |. 8 B83 D0020000 mov eax,dword ptr ds:[ebx+0 x2 D0 ]00442D80 |. 8078 47 01 cmp byte ptr ds:[eax+0 x47 ],0 x1 ; 熟悉的地址00442D84 |. 75 12 jnz short aLoNg3 x_.00442 D98 00442D86 |. BA 002 E4400 mov edx,aLoNg3 x_.00442 E00 ; UNICODE "0" 00442D8B |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442D91 |. E8 5 A05 FEFF call aLoNg3 x_.004232 F0 00442D96 |. EB 3 F jmp short aLoNg3 x_.00442 DD7 00442D98 |> 8 D55 FC lea edx,dword ptr ss:[ebp-0 x4 ]00442D9B |. 8 B83 E0020000 mov eax,dword ptr ds:[ebx+0 x2 E0 ]00442DA1 |. E8 1 A05 FEFF call aLoNg3 x_.004232 C0 00442DA6 |. 8 B45 FC mov eax,dword ptr ss:[ebp-0 x4 ]00442DA9 |. E8 C248 FCFF call aLoNg3 x_.00407670 00442DAE |. 50 push eax00442DAF |. 8 D55 FC lea edx,dword ptr ss:[ebp-0 x4 ]00442DB2 |. 8 B83 DC020000 mov eax,dword ptr ds:[ebx+0 x2 DC]00442DB8 |. E8 0305 FEFF call aLoNg3 x_.004232 C0 00442DBD |. 8 B45 FC mov eax,dword ptr ss:[ebp-0 x4 ]00442DC0 |. 5 A pop edx ; 0018 F8 D4 00442DC1 |. E8 DAFDFFFF call aLoNg3 x_.00442 BA0 ; 算法00442DC6 |. 84 C0 test al,al00442DC8 |. 74 0 D je short aLoNg3 x_.00442 DD7 00442DCA |. 33 D2 xor edx,edx00442DCC |. 8 B83 CC020000 mov eax,dword ptr ds:[ebx+0 x2 CC]00442DD2 |. E8 D903 FEFF call aLoNg3 x_.004231 B0 00442DD7 |> 33 C0 xor eax,eax00442DD9 |. 5 A pop edx ; 0018 F8 D4 00442DDA |. 59 pop ecx ; 0018 F8 D4 00442DDB |. 59 pop ecx ; 0018 F8 D4 00442DDC |. 64 :8910 mov dword ptr fs:[eax],edx00442DDF |. 68 F42 D4400 push aLoNg3 x_.00442 DF4 00442DE4 |> 8 D45 FC lea eax,dword ptr ss:[ebp-0 x4 ]00442DE7 |. E8 CC09 FCFF call aLoNg3 x_.004037 B8 00442DEC \. C3 retn
进入算法进行查看,可以看到一个通过注册码求用户名的过程。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 00442C09 |. 0 FB64430 FF |movzx eax,byte ptr ds:[eax+esi-0 x1 ] ; 获取最后一位00442C0E |. F7 E8 |imul eax ; 平方00442C10 |. 0 FBFC0 |movsx eax,ax00442C13 |. F7 EE |imul esi ; 乘以长度/长度不断-1 00442C15 |. B9 19000000 |mov ecx,0 x19 00442C1A |. 99 |cdq00442C1B |. F7 F9 |idiv ecx00442C1D |. 83 C2 41 |add edx,0 x41 ; 除以0 x19 余数+0 x41 00442C20 |. 58 |pop eax ; 0018 F8 D4 00442C21 |. 8810 |mov byte ptr ds:[eax],dl00442C23 |. 4 E |dec esi00442C24 |. 85 F6 |test esi,esi00442C26 |.^ 75 D1 \jnz short aLoNg3 x_.00442 BF9 00442C28 |> 8 B45 F4 mov eax,dword ptr ss:[ebp-0 xC]00442C2B |. 8 B55 FC mov edx,dword ptr ss:[ebp-0 x4 ]00442C2E |. E8 110 FFCFF call aLoNg3 x_.00403 B44 ; 与输入的用户名进行比较00442C33 |. 75 17 jnz short aLoNg3 x_.00442 C4 C
代码如下:
char name[20 ];10 );int len = strlen (name);int a = len;for (int i = 0 ; i < len; i++) {int temp = name[a-1 ] * name[a-1 ];0x19 ;0x41 ;1 ] = temp;1 ;printf ("%s\n" , name);
现在就剩下最后一个事件,CancellaClick
进去查看,发现里面没有那个熟悉的地址,那么基本上那个地址的赋值应该就是在这里了吧,只有一个跳转,修改条件后,最早下的硬件断点终于断下来了。那么查看一下算法的过程。
进入函数查看,可以看到具体的算法,是一个通过用户名求注册码的过程。
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 00442B20 |. 83F8 05 cmp eax,0x5 ; 判断输入的name是否大于5 00442B23 |. 7E 53 jle short aLoNg3x_.00442B78 00442B25 |. 8B45 FC mov eax,dword ptr ss:[ebp-0x4 ]00442B28 |. 0FB640 04 movzx eax,byte ptr ds:[eax+0x4 ] ; 获取name第五位00442B2C |. B9 07000000 mov ecx,0x7 00442B31 |. 33D2 xor edx,edx00442B33 |. F7F1 div ecx ; 除以7 00442B35 |. 8BC2 mov eax,edx ; 余数00442B37 |. 83C0 02 add eax,0x2 00442B3A |. E8 E1FEFFFF call aLoNg3x_.00442A20 ; 阶乘00442B3F |. 8BF0 mov esi,eax00442B41 |. 33DB xor ebx,ebx00442B43 |. 8B45 FC mov eax,dword ptr ss:[ebp-0x4 ]00442B46 |. E8 E90EFCFF call aLoNg3x_.00403A34 00442B4B |. 85C0 test eax,eax00442B4D |. 7E 16 jle short aLoNg3x_.00442B65 00442B4F |. BA 01000000 mov edx,0x1 00442B54 |> 8B4D FC /mov ecx,dword ptr ss:[ebp-0x4 ]00442B57 |. 0FB64C11 FF |movzx ecx,byte ptr ds:[ecx+edx-0x1 ] ; 逐位获取00442B5C |. 0FAFCE |imul ecx,esi00442B5F |. 03D9 |add ebx,ecx ; user32.75B16D5100442B61 |. 42 |inc edx00442B62 |. 48 |dec eax00442B63 |.^ 75 EF \jnz short aLoNg3x_.00442B54 00442B65 |> 2B5D F8 sub ebx,dword ptr ss:[ebp-0x8 ] ; 减去注册码十六进制00442B68 |. 81FB 697A0000 cmp ebx,0x7A69 00442B6E |. 75 04 jnz short aLoNg3x_.00442B74 00442B70 |. B3 01 mov bl,0x1 ; 关键的赋值00442B72 |. EB 06 jmp short aLoNg3x_.00442B7A 00442B74 |> 33DB xor ebx,ebx00442B76 |. EB 02 jmp short aLoNg3x_.00442B7A
代码如下:
int a = szname[4 ] % 0x7 ;2 ;int num = 1 ;for (int i = 1 ; i <= a; i++) {int len = strlen (szname);int sum = 0 ;for (int i = 0 ; i < len; i++) {int serial;0x7A69 ;printf ("%d\n" , serial);return serial;
当经过了这个判断之后,那个地址就会被赋值,同时cancle按钮也会消失,ok按钮会常亮。
那么整体的流程就很清楚,首先要通过用户名计算一个注册码输入cancle按钮消失,ok变亮,然后再通过注册码计算出一个用户名输入后,ok消失,完成注册
注册机编写 完整注册机代码如下:
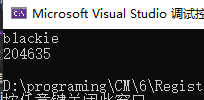
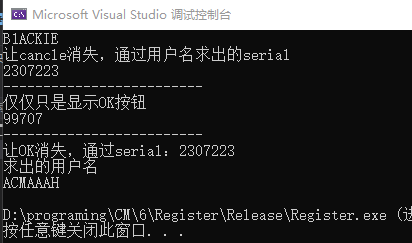
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 #include <stdio.h> #include <Windows.h> #include <string.h> int CancleClick (char * szname) int a = szname[4 ] % 0x7 ;2 ;int num = 1 ;for (int i = 1 ; i <= a; i++) {int len = strlen (szname);int sum = 0 ;for (int i = 0 ; i < len; i++) {int serial;0x7A69 ;printf ("%d\n" , serial);return serial;void CodiceChange (char * szname) int len = strlen (szname);int sum = len;int temp = 1 ;for (int i = 0 ; i < len - 1 ; i++) {1 ]) * temp) + sum;int serial;0x29A ;printf ("%d\n" , serial);void OkClick (int serial) char name[20 ];10 );int len = strlen (name);int a = len;for (int i = 0 ; i < len; i++) {int temp = name[a-1 ] * name[a-1 ];0x19 ;0x41 ;1 ] = temp;1 ;printf ("%s\n" , name);int main () char name[20 ];20 );printf ("让cancle消失,通过用户名求出的serial\n" );int serial = CancleClick(name);printf ("-------------------------\n" );printf ("仅仅只是显示OK按钮\n" );printf ("-------------------------\n" );printf ("让OK消失,通过serial:%d\n求出的用户名\n" ,serial);return 0 ;
cancle按钮
OK按钮
总结 程序共有三个算法
nomechange和codicechange里的,仅仅只是让OK亮起来
cancleClick里的,消失cancle按钮,赋值给那个关键地方,OK亮起
OKClick里的,让OK按钮消失
不知道nomechange和codicechange里的算法有什么用,感觉没必要。。。